Secure development and coding training
Online course with own lab environment for practical exercises
Customers who strengthen their security with Cyber LABs
Better trained developers than software with RCE vulnerabilities

Chapter overview Module 1: Secure Development Lifecycle
Intro & Let’s hack
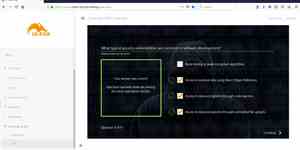
Introduction & Basics: How does the training work. Why is security so important throughout the software development lifecycle.
Plus some hacking to get warm: LAB exercise on bad exception handling and password cracking. The exercise shows which effects even inconspicuous security holes can have.
Security Basics
Clarification of the most important basic terms
- The protection goals in the CIA Triad: Confidentiality, Integrity and Availability.
- The security principles to achieve these CIA security goals: Don't trust any input, keep security simple, minimize the attack surface, implement 'Defense in Depth', use minimal rights, be 'Secure by Default' and always solve security problems properly.
Implementation phase
- Authentication: What mistakes are often made during authentication and what simple methods can be used to significantly increase security.
- Authorization (access control): what is the difference to authentication. LAB exercise Accessing data via Direct Object Reference. How to prevent such vulnerabilities and how to implement appropriate access control.
- Session Management: What threats exist around session management. LAB exercise Adoption of a Session by Session Fixation. How to make session management secure.
- Input Validation, Output Sanitization and Injection: What is an injection and what types are there? LAB exercise Data manipulation and deletion by SQL injection. How can injections be prevented.
- Cross Site Scripting: What types of Cross Site Scripting are available. LAB exercise on persistent cross site scripting. Which defense measures are effective.
- Cryptography & Secrets Management: What types of secrets exist and what forms do they take ("at rest", "in transit" and "in memory"). LAB exercise System Access via File Inclusion. What is the difference between encryption and encoding. LAB Exercise Decoding a password in a config file. Tips for handling secrets.
- Remote Code Execution: LAB exercise web shell upload. Why do RCE vulnerabilities have such catastrophic effects. How can the "Defence in Depth" approach reduce such effects.
- Exceptions & Error Handling: How do hackers exploit error messages and error routines? How should secure error handling look like.
- Application Logging: Why is a good logging strategy elementary and what should better not be logged. LAB exercise on confidential data in log files. Tips on how to achieve good logging.
- Secure Networking and Infrastructure: Hackers attack systems, not software. What are the weaknesses in transmission protocols and why are hardening and patching not just the job of administrators?
Validation phase
- Code Reviews: what security best practices exist and when should a source code review be performed.
- Automated Code Analysis: what are the benefits of automated code analysis and which modules can be analyzed.
- Vulnerability scans: What are the benefits of automated vulnerability scans and where are their limits.
- Penetration tests: why are penetration tests sometimes indispensable.
Operation phase
- Code Changes: what effects do code changes have on security. Which measures should be taken.
- Configuration: how does the configuration influence the security.
- Patch Management: Who is responsible for patching systems and to where. LAB exercise Exploitation of another RCE vulnerability through an outdated library.
- Decommissioning: What steps to take when a system is 'End of Life'.
Chapter overview Module 2: Cloud Security & DevSecOps
Cloud Security
Cloud security: The operating models in the cloud
Shared responsibility: Role of the admin and the cloud provider
Tips for the Cloud: Clean account separation. Securing privileged accounts, jump server concept. Various multi-factor methods. Private networks and IP restrictions
LAB exercise: Access to poorly configured cloud database through OSINT research
DevSecOps
- The concept behind DevSecOps: a win-win-win situation.
- Automated security checks: How to permanently eliminate vulnerabilities with functional tests, code scanners and co.
- Infrastructure as code: Code is code - and therefore susceptible to vulnerabilities. Tips for secret handling and security checks in IaC.
Lab exercise: Reading secrets from the state of an IaC project.
Customer feedback

The next steps: How to get the most out of your Cyber LAB
Our Secure Development training for developers lays the right foundation for secure application development: Product managers, application owners, software architects and developers understand why secure development is fundamentally important and which components are essential prerequisites.
However, this enthusiasm for security must then be properly channelled so that secure development actually becomes a sustainable part of everyday development.
How do you do that? Here you will find our proven best-practice approach for firmly embedding security into your development process.